Thursday, May 25, 2017
How to Concatenate Join and Sort Array in JavaScript
How to Concatenate Join and Sort Array in JavaScript
How to Join Two Arrays using Concat()
var array1=new Array(3);
array1[0]="Saab"
array1[1]="Volvo"
array1[2]="BMW"
var array2=new Array(3);
array2[0]="Yamaha"
array2[1]="Honda"
array2[2]="Bajaj"
var array3=array1.concat(array2);
for(i=0; i<array3.length;i++)
{
document.write(array3[i]+"<br/>")
}
</script>
Preview:
How to Put Array Elements Into a String using Join()
Preview:
How to Sort String Array using sort()
Preview:
How to Sort Numeric Array using sort()
Preview:
- pop(): Removes and returns the last element of an array
- push(): Adds one or more elements to the end of an array and returns the new length.
- reverse(): Reverses the order of the elements in an array
- toString(): Converts an array to string and returns the result.
Read Next:How to use Round, Random, Min and Max in JavaSript
Related Search Terms
Concate Array in JavaScript
Join Array in JavaScript
Sort Array in JavaScript
Related Posts:
How to Show Pop Up Boxes Using JavaScript?
How to Write Conditional Statements in JavaScript?
How to Write JavaScript With HTML?
How to Loop using JavaScript?
Image Slideshow with Navigation Buttons Using JavaScript
How to create Changeable Date and Time Using JavaScript?
How to Create JavaScript Image Slideshow with LInks
How to Display Date Format in JavaScript?
How to Validate a HTML Form Using JavaScript?
What are the Different Ways to Redirect Page in JavaScript?
How to Detect Visitors Browser Using JavaScript?
How to make rounded corners border using CSS
How to Create Custom CSS Template for Printing
How to create a simple form using HTML?
Go to link Download
Tuesday, May 23, 2017
How to buy apps in the android market or play store using a credit card
How to buy apps in the android market or play store using a credit card
How to buy apps in the android market or play store using a credit card - Even though many android apps are free, but sometimes there are also interesting applications yet paid, for those of you who use credit cards here are the steps to make a purchase through the app store play.
Make sure your credit card is issued by active local bank. Or if you have a debit card, the card must be valid internationally. And supported google wallet, usually type VISA / Mastercard. Record Number of credit cards, note cards behind the three numbers, and month / year expired.
For example:
Card No.: 1234 5678 9012 3456
No. On the back of the card: 123
Expired: 12/99
Open the application you want to buy.
Click on a price, then you will go into google wallet, just click proceed.
Complete input your card details, name and address of card suits, and phone numbers.
If it is then your card is ready for use, is there a charge, if based on the info from google wallet here -> http://www.google.com/wallet/faq.html use charge cards are not charged a penny, so you will be charged according to the application fee purchased. Well if it is active. Then you can buy the application directly.
Fill in your password (email password that you use to play store), if it is okay. Then the application can be downloaded directly purchased.
Well done, for now you can directly buy the application, if the application is purchased, in the handset anywhere in the home account status will remain the same then purchased.
So if you do not like the application, whether it can refund, yes for the application you are able to do a preview, if it does not fit anymore open the program and click refund (the same with the delete key applications). And the refund is active about 15 minutes. If after 15 minutes through the refund process should report to the developer and of course more complicated. For clarity -> http://support.google.com/googleplay/bin/answer.py?hl=en&answer=134336
Happy shopping, do not be wasteful. And do not be late to pay bills that are not subject to interest.
Hopefully useful.
Go to link Download
Friday, May 19, 2017
Google defeats Oracle in Java code copyright case
Google defeats Oracle in Java code copyright case
Google has won a major US court battle with software firm Oracle after a jury rule

Oracle had argued that Google had infringed its copyright and had sought nearly $9bn (£6bn) in damages.
The outcome was eagerly awaited by software developers who feared that a victory for Oracle might encourage more such legal actions.
The company says it will appeal against the decision.
Google uses Java in its Android smartphone operating system which powers about 80% of the worlds mobile devices.
The company had argued that extending copyright protection to pieces of code called APIs (application programming interfaces) would threaten innovation.
The jury in San Francisco agreed that copyright law allowed "fair use" of the Java elements as they were only a part of a larger system Google had created for a new purpose.
"Todays verdict that Android makes fair use of Java APIs represents a win for the Android ecosystem, for the Java programming community, and for software developers who rely on open and free programming languages to build innovative consumer products," a Google spokesperson said in an emailed statement.

The legal battle began in 2010 and the two firms first faced each other in court in May 2012. A federal judge ruled against Oracle, but the company then appealed. After legal wrangling, the case was sent back to court.
Despite Thursdays outcome, Oracle lawyer Dorian Daley said it would pursue the matter further.
"We strongly believe that Google developed Android by illegally copying core Java technology to rush into the mobile device market," he said.
"Oracle brought this lawsuit to put a stop to Googles illegal behaviour. We believe there are numerous grounds for appeal and we plan to bring this case back to the federal circuit on appeal."
Go to link Download
Friday, May 12, 2017
How To Do SEO In 2014
How To Do SEO In 2014

The question needs to be answered by analysing ranking in 2013 and then build on factors producing positive effects. Search engines have definitely taken major steps to stop spam from adversely affecting search experience. Time spent on a website is money for the search engines, as visitors are likely to click on a paid ad.
Increasing Role Of Social Signals
One way of enhancing experience is to provide a platform that encourages shared content, which is why social networking is gaining ground. Search engines established parameters to recognise good content strategy associated with ethical SEO including social signals derived from active engagement, authorship or value of content directly connected to the author, regular updates recognised by increasing readership, and frequent updates giving signs of a healthy website. Relevance does play an important part, and businesses recognise the fact they need to build authority where it matters.Content Strategy For SEO In 2014
Debate on whether content plays an important role is no longer valid. Search engines have indicated in clear terms fresh information is relevant. The question then arises whether good SEO content strategy involves writing long or short articles. If other factors are analysed, relevance is definitely given to good content keeping visitors glued to the website. Articles averaging 2,000 words are finding prime spots in Google search. However, due consideration must be given to the fact mobile users have increased tremendously, and it is a bit difficult to read long articles on a smart phone.The long-term strategy is valid, as tablet sales are on the rise. Developing content strategy for 2014 is a must, and the logical way to go about it is to generate more interest among visitors to build a strong fan base for the long term. Will content in specific niches play a dominant role depending on user interest? Ideally, a wait-and-watch approach is warranted inclined towards following leaders in the same niche.
People frown upon guest blogging as a Black Hat strategy no longer having relevance in 2014, which is far from the truth. Quality back links will play a vital role in improving rankings, and one way to look at getting links from authority sites is to continue writing relevant content.
The concept is changed a bit wherein high quality content finds natural resources in authority sites willingly offering to share the author’s content. In other words, the author does make a difference, both in the eyes of an authority site and search engine. A good author readily finds resources to post an article. The next link is always easier, as other sites recognise value in promoting what the authority writer now has to offer.
Go to link Download
Wednesday, May 10, 2017
How To Earn Up To 10 In A Day On Android Phone Complete Guide
How To Earn Up To 10 In A Day On Android Phone Complete Guide

Have you ever wondered, “Can I earn $50 a day just by playing on my android?”. Well if not, here is an app for you – Whaff!. Just download application or use them and earn loads of money, just sitting!
This is a wonderful application for people who want to get apps in cheaper price or earn cash after downloading any free apps. If you have ever hesitated to find apps of this kind, you need no more hesitations with this fantastic application.
Warning!:
- Please do not use any VPN Service as it might ban you forever.
- Using VPN is against the Rules and Regulations of Whaff. So if you use VPN, and get banned, I am not to be blamed under any circumstaces.
Features:
- Get rewards for downloading any app.
- Get rewards for using the app.
- Get rewards for maintaining the app on your device.
- NEW! –> Get huge rewards for opening Whaff Rewards App and checking your attendance daily!
How To Use?
- Download the APK file from below.
- Install the app on your Android Smartphone.
- Login with your ORIGINAL Facebook Account.
- Done! Enjoy earning money with this free app.
Screenshots:


Payment Proof:

How To Get A $0.30 Bonus!
- Just go to Browse tab in the extreme left side.
- Click friends invite.
- Enter the code: BJ00408
- And Get 0.30$ Free

Download Links:
Google Play| Whaff Rewards v2.0 APK | Mirror
Go to link Download
Tuesday, May 9, 2017
How to boot live USB in VirtualBox
How to boot live USB in VirtualBox
In this tutorial, we will show you a way for making VirtualBox or VMware Player boot from live USB devices since this feature hasnt been implemented yet natively in both software. The trick we will use will rely on the Plop boot manager which allows via a live iso to boot from USB devices.

We will show you how to use the Plop boot manager with both VMware Player and VirtualBox under Ubuntu/Linux Mint (12.10/12.04/Mint 14/13, etc.).
Downloading the Plop Boot Manager
You can download the Plop iso file from here. Or Open the terminal and download the Plop iso image to your home directory with this command:
cd && wget -c http://goo.gl/sJoKf -O ploplinux-4.2.2.iso
1. Boot from Live USB in VirtualBox
We assume you have already created a VM (virtual machine), double click it to start it. Mount the USB stick (live USB) to VirtualBox by opening Devices >>USB Devices >> Your USB Device:

If it is not available, then you may need to run this command from the terminal to be able to mount USB devices under Ubuntu/Linux Mint (replaceusername with your own user account name):
sudo adduser username vboxusers
Once your USB device is mounted in VirtualBox, look at the bottom of the VMs window, you will see a small CD icon, right-click it and select "Choose a virtual CD/DVD disk file":

Select now the plob iso file (ploplinux-4.2.2.iso) that you have downloaded:

Press Right CTRL+R to reset the VM and wait for Plop boot menu. If it didnt show up, reset the VM again and press F12 to bring up the boot menu, pressc to boot from CD-ROM:

In the Plop boot menu, use your arrow keys to select the "Plop Boot Manager" option and press Enter:

Another menu will show up, select USB and press Enter to boot from the USB device:

2. Boot from Live USB in VMware Player
To boot from a live USB in VMware Player, we will also use the Plop boot loader. Start VMware Player, select any VM of your choice, then click "Edit Virtual machine settings":

Select the "CD/DVD (IDE) option, then in the right side, select "Use ISO image" and click the Browse button:

Open the Plop iso file and click Save:

Start now the VM and wait for the Plop boot menu. When it shows up, selectPlop Boot Manager and press Enter:

In the next menu, select USB and press Enter to boot from the USB device:

Go to link Download
Sunday, May 7, 2017
Thursday, May 4, 2017
Identify the Hardware installed in your computer to find its driver
Identify the Hardware installed in your computer to find its driver
So after windows installation you could get into trouble if the device driver is not found or can not be installed automatically because that device would stop working.So here are the steps to get that issue fixed.
Option 1
Step 1. Open device manager by typing Devmgmt.msc at run.
Step 2. Right mouse click on the unknown device and select properties.
Step 3. On the device properties window click on the Details tab and select Hardware Ids.
 |
| Pic-18(a) |
Step 4. Here you only need to note down these two information highlighted in the rectangle shown in the above picture-18(a).So as shown in the picture above note down VEN( Vendor ID) -168C ( as shown in the above picture) and DEV ( Part/Device ID )- 0032 as per the above picture.
Step 5. Go to website http://www.pcidatabase.com/ and then under vendor search Type the Vendor ID as 168C or whatever it shows in your device properties windows for that unknown hardware, and then hit search.
 |
| Pic-18(b) |
 |
| Pic-18(d) |
Step 7. so you will need to find the device with code mentioned in the Hardware Ids as DEV which is 0032 in my case.
 |
| Pic-18(e) |
Option 2
Option two is the easiest and best way to identify the unknown device.There is this tool name Hardware Identify from Tweaking.com.you can download it from the download tab of my blog or click here.
Tweaking.com - Hardware Identify will help identify unknown hardware on your system. This program does not help you download drivers but helps let you know what the hardware is so you know what drivers to find.
For example say you just reinstalled a computer and the device manager shows multiple unknown hardware with no drivers installed. Well you dont know what drivers to find since you dont know what the hardware is. Now with Tweaking.com - Hardware Identify you can see what that hardware is.
The program also has a easy option to help improve the device database. Once you have all drivers installed you can have the program check for any hardware on the system that isnt in the database and submit it to Tweaking.com. With in a few days the database will be updated and the device list will grow with the help of users like you!
Picture below was taken from Tweaking .com for the educational and instructional purposes.
 |
| Pic-18(f) |
..
Note: Any suggestion or comments to improve this article is very welcome and appreciated.Please write to me at nasir@simulato.com in case you have any queries.
People also read following top most searched issue
Go to link Download
Thursday, April 27, 2017
How To Increase The Internet Speed in PC
How To Increase The Internet Speed in PC

And when it fails to deliver, there’s no telling how worse it could be.
The slow net scenario
Now, at an era largely characterised by instant gratification, the sight of a loading icon – the circling arrow or the bar of green – could inspire automatic groans. Nobody wants them, unless this slow net thing is epidemic in your neighbourhood.What are the causes of this slow internet connection? About.com’s “Internet for Beginners” has identified at least thirteen (13) causes.
- Poor hardware
- Incorrect router configuration
- Leeching internet users
- Un-upgraded NIC
- Spyware/malware infection
- Downloads
- ISP’s routing signals
- Outdated DNS
- Full browser memory cache
- Devices disrupt signals
- Old PC
- Open windows
- Unattended dialog box
Faster than energy bunnies
There are many ways of increasing your internet connections speed. The best way to do it is to start with diagnosis. See through those aforementioned causes and learn which among those are causing your internet speed to drop.Through a determined cause, you are able to appropriate a targeted solution. For instance, if the problem is caused by poor hardware, then you can purchase a newer and better model. If it’s about the incorrect router configuration, try to correct it or tap your friendly IT expert to do the works.
Or if the culprit of the internet snail-pace is your leeching neighbours (most likely the case for Wi-Fi connections), strengthen your connection’s password and utilise other security features. Infections, on the other hand, could be fixed through stringent scanning software.
Obviously, the nature of addressing your internet connection speed has something to do with the basics: consistent upgrades and investment in clearing ups. All of these serve to speed up that connection, probably faster than the proverbial energy bunnies.
Tech buddies
Apart from those, don’t skimp on tech savvy relationships. Try to foster a friendly (and not hostile) bond with that tech – the ones from the hardware distributor, the internet connection provider, the tech support team, and so on.They’re your key to the better world of lightning speed connection. And though you might approach them for professional service, they would be willing to extend support if you’re consistently nice to them.
Awakened consciousness
Lastly, to increase the speed of your internet connection, try not to do things that could disrupt it. Avoid these disruptive things if it can be helped. And if the PC or any other device is shared among the members of the family, encourage them to perform the same measures.Image Credit: ddpavumba
Go to link Download
Sunday, April 23, 2017
How to get the all opened tab back in Google Chrome if you have closed all the tab by mistake
How to get the all opened tab back in Google Chrome if you have closed all the tab by mistake
This is just for an information I am sure most of you must know it already.I wanted to let you know how you can get all the opened tab in Google Chrome back if you have closed all the tab by mistake, because when you manually close it, you dont get the option of restore so if you dont get the restore option here is how you can get all those opened tab back.
Get all opened pages that you were working on back
1. Open chrome and click on the three small parallel lines on the top right hand side and then move to Recent Tab and click the no. of Tab option so here in this picture it shows 9 Tab because I had 9 tabs opened before closing the Chrome.
So click on the 9 Tab.
OR
Just press Ctrl+Shift+T.
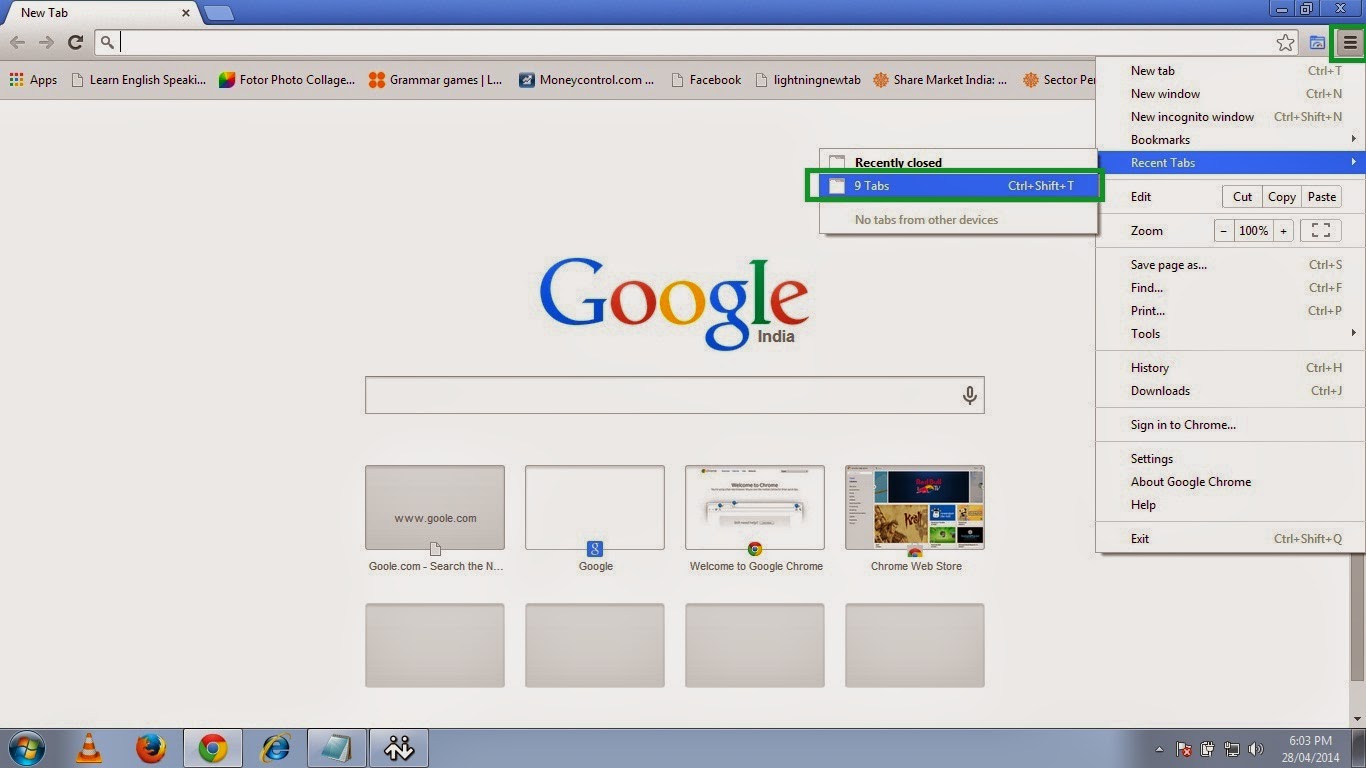 |
| Pic-14(a) |
2. And then it will open all previously opened tabs with the webpages you were browsing.
 |
| Pic-14(b) |
Happy Learning
Nasir
People Also read my Following Posts.
Get a Website ups and running @ $2.95
What is a website and how is it accessed on the web?How to build and host it free?
How to Speed up your computer 20 Times faster.
Restore and Reset your iPhone, iPad or iPod back to the original Factory Default Settings.
Go to link Download
Friday, April 21, 2017
IBM builds a service to help you know who to trust in the cloud
IBM builds a service to help you know who to trust in the cloud
Go to link Download
Wednesday, April 19, 2017
How to Write in Urdu anywhere in Computer for all systems
How to Write in Urdu anywhere in Computer for all systems
in few setups....

Go to link Download
Tuesday, April 18, 2017
How to Resolve After Removing Maximum Memory in MSCONFIG The boot is not as fast before I first enabled it
How to Resolve After Removing Maximum Memory in MSCONFIG The boot is not as fast before I first enabled it
After Removing Maximum Memory in MSCONFIG, The boot is not as fast before I first enabled it...
I have a HP Compaq 6720s...
Windows 7 Professional X 64bit
My specs are :
Intel Core 2 Duo
2X2GB DDR3
1X120GB FUJITSU Hard Drive
Intel X3100 Graphics Media Accelerator
Intel PRO Wireless 3945 ABG
Before I enabled it, it took about 40 ( 5 secs stall on HP logo ) secs to boot, now it takes about 1 min and 30 sec to boot ( stalls for about 30 secs on the HP logo )...
WTF did microsoft do to my PC??? I dont want to restore my PC again because I have a lot of data and that I have already restored Windows 7 Pro alone on this PC 8 times and I learnt somewhere that restoring it too much is bad for a old hard drive like
mine.
Anwsers to the Problem After Removing Maximum Memory in MSCONFIG, The boot is not as fast before I first enabled it...
Download Error Fixer for Free Now
Hi,
What made you to remove maximum memory setting in msconfig?
Let’s try the troubleshooting steps mentioned below:
Method 1: Open the Performance troubleshooter
http://windows.microsoft.com/en-us/windows7/Open-the-Performance-troubleshooter
Method 2: Boot the computer in safe mode and check whether the issue persists, if the issue does not persist then perform clean boot and check whether the issue resolves.
Safe mode starts Windows with a limited set of files and drivers.
Startup programs dont run in safe mode, and only the basic drivers needed to start Windows are installed.
Please click on the mentioned link below.
http://windows.microsoft.com/en-US/windows-vista/Start-your-computer-in-safe-mode
Method 3: To help troubleshoot error messages and other issues, you can start Windows by using a minimal set of drivers and startup programs.
This kind of startup is known as a "clean boot." A clean boot helps eliminate software
conflicts.
Note When you perform a clean boot, you may temporarily lose some functionality.
When you start the computer as usual, the functionality returns.
However, you may receive the original error message, or you may experience the original
behavior.
Note: Follow step 7 to reset the computer to start as usual after the clean boot process.
http://support.microsoft.com/kb/929135
Refer: Optimize Windows 7 for better performance
Click on the link mentioned and check if it helps.
http://windows.microsoft.com/en-us/windows7/Optimize-Windows-7-for-better-performance
Hope it helps.
Open Action Center by clicking the Start button Picture of the Start button, clicking Control Panel, and then, under System and Security, clicking Review your computers status.
Make sure your computer has at least the minimum amount of random access memory (RAM) required to run the program that is displaying the error. Look for the program requirements online or in the packaging information.
Recommended Method to Fix the Problem: After Removing Maximum Memory in MSCONFIG, The boot is not as fast before I first enabled it...:
How to Fix After Removing Maximum Memory in MSCONFIG, The boot is not as fast before I first enabled it... with SmartPCFixer?
1. You can Download Error Fixer here. Install it on your system. When you open it, it will perform a scan.
2. After the scan is done, you can see the errors and problems which need to be fixed.
3. The Fixing part is done, the speed of your computer will be much higher than before and the errors have been removed.
Related: ,[Solution] Error Clean,Solution to Error: mozilla thunderbird not responding windows 7,Fast Solution to Error: 0x00405da8,Troubleshoot:Toolbar,Solution to Problem: Windows Media Player C00d1199 Windows 7,Solution to Error: Windows 7Function,Troubleshooting:Pc Code 9999 Error,Solution to Problem: Norton Svchost Exe Virus,[Anwsered] Error 2738
Read More: How to Fix Problem - After Windows 7 SP1 Update - applications fail to start because side by side configuration is incorrect?,Troubleshooting:After typing a searching word and press enter, nothing happens. Hovering over the headlines with a mouse doesnt change anything.,[Solution] After reinstall, my windows seems to periodically freeze and unfreeze,Tech Support: After Windows 7 SP1 Store to Ram (STR) sleep mode S3 does not work,[Solved] after running microsoft disk cleaner it showed in would free up 1.3 GB so I ran it, now I did again and it says 2.2 GB to free up??? Where is all this junk comiong from all the time??,32 bit printer drivers for Windows 7 64 bit OS,Activecell range 2 columns loop until last column,about pc battery power,Acrobat Reader downlode also automatically downloaded McAfee Security Plus...question about this below.,A runtime error has occurred. example: Line32 Do you wish to DeBug?
Go to link Download
Sunday, April 16, 2017
Historical Findings in Astronomy
Historical Findings in Astronomy
Created by Labroots, the leading social networking website for scientists, engineers, and other technical professionals.
Go to link Download
Sunday, April 9, 2017
How Fords autonomous cars can see in the dark
How Fords autonomous cars can see in the dark
Go to link Download
